Introduction
Unseen and unpredictable, zero-day threats loom as a constant menace to modern businesses. Detecting and mitigating these stealthy attacks is essential to safeguard your business infrastructure and data. In this blog, we explore effective techniques and best practices to identify and counter zero-day threats effectively. Arm yourself with knowledge and proactive measures to fortify your organization’s security defenses and defend against the unseen dangers that could otherwise jeopardize your business. Let’s delve into the world of zero-day threat detection and mitigation to bolster your cyber resilience.
Understanding Zero-day Threats
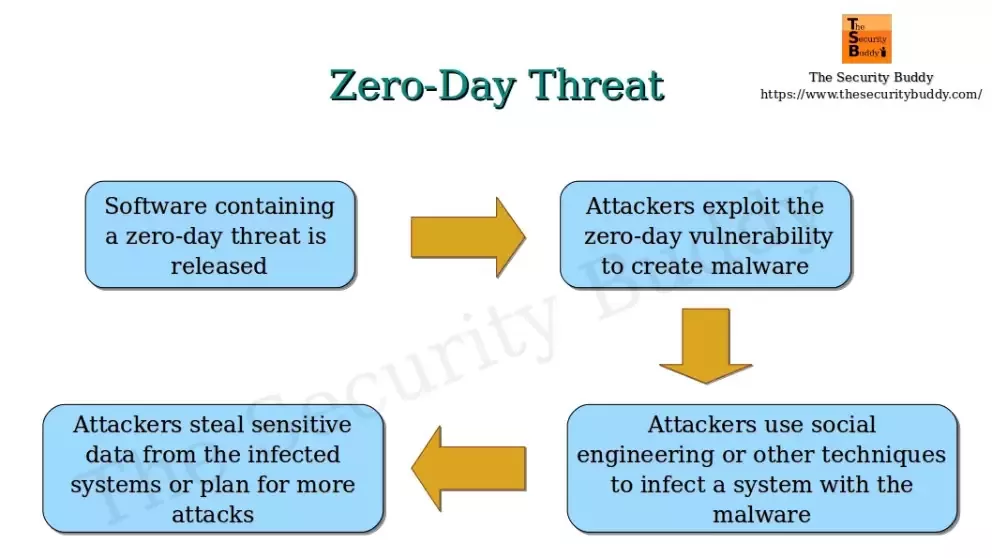
Zero-day threats refer to previously unknown vulnerabilities in software or systems that can be exploited by attackers before a patch or solution is available. They are called “zero-day” because developers have zero days to prepare a defense against them. These vulnerabilities can exist for weeks, months, or even years before being discovered. According to a report by Symantec, in 2021, an average of 18 zero-day vulnerabilities were discovered per month, highlighting the magnitude of the issue.
https://computersecuritypgp.blogspot.com/2016/06/what-is-zero-day-threat.html
In 2022, there were over 150 publicly disclosed zero-day vulnerabilities, and this number is expected to grow in the coming years.

https://www.manageengine.com/log-management/cyber-security/what-is-zero-day-exploit.html
The Risks of Zero-Day Attacks
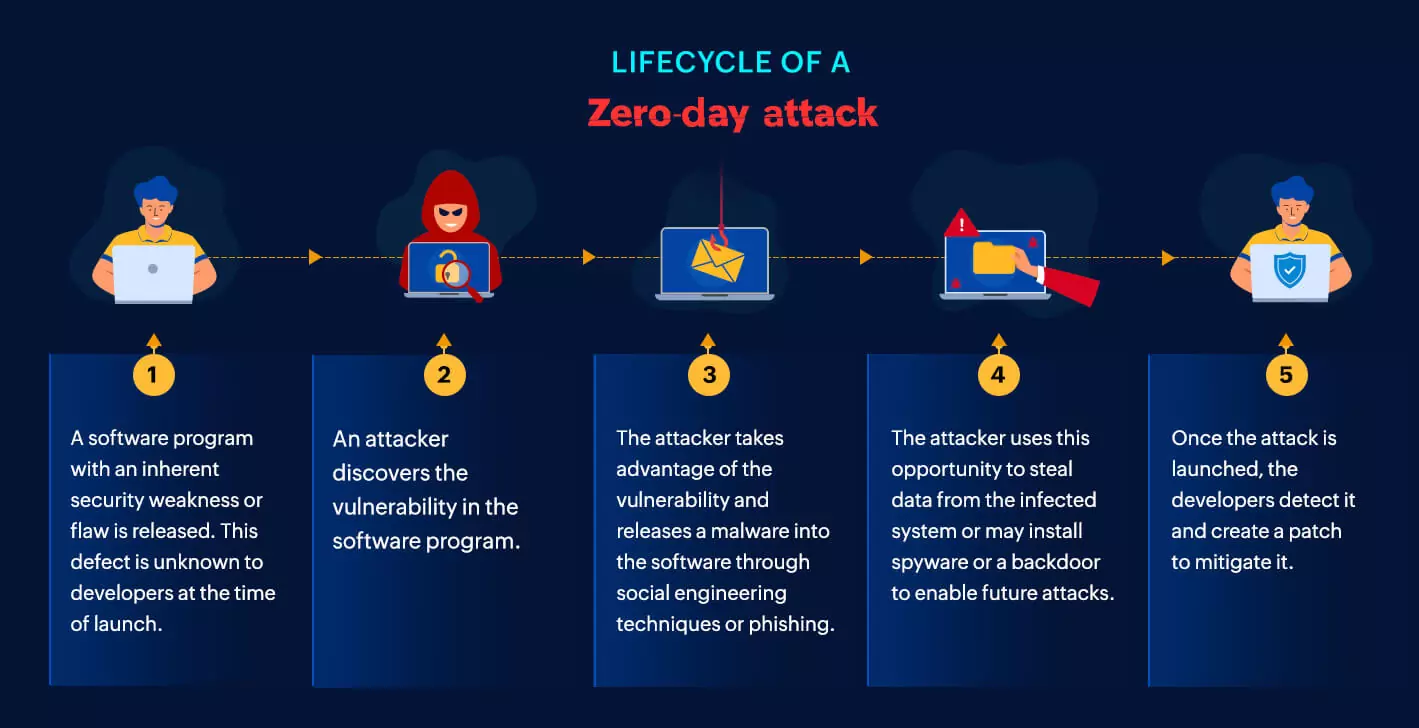
Zero-day attacks can pose a significant risk to businesses of all sizes. They can be used to steal sensitive data, disrupt operations, or even take control of critical systems. In some cases, zero-day attacks have been used to cause physical damage, such as the Stuxnet attack that targeted Iran’s nuclear program.
Here are some of the risks of zero-day attacks:
Control of critical systems:
Used to take control of critical systems, such as industrial control systems or power grids. This could lead to physical damage or loss of life.
Unpredictable exploits:
Zero-day attacks leverage undisclosed vulnerabilities, leaving defenders unprepared to counter the new threat, leading to potential system breaches and data compromise.
No available patch:
Since zero-day vulnerabilities are unknown to software vendors, there is no immediate fix or patch to safeguard systems from these attacks.
System vulnerabilities exposed:
Zero-day vulnerability pinpoints and exploits specific weaknesses in software or hardware, leaving systems susceptible to infiltration and unauthorized access.
Targeted attacks:
Cybercriminals often deploy zero-day exploits with precision against high-value targets, such as governments, corporations, or individuals, aiming for maximum impact.
Stealthy and undetectable:
Zero-day attacks evade traditional security measures and intrusion detection systems, remaining hidden until their effects are devastatingly apparent.
Rapidly spreading malware:
Exploiting zero-day vulnerabilities allows malware to propagate swiftly through networks, amplifying the scale and severity of the attack.
Data theft:
Zero-day attacks can be used to steal sensitive data, such as customer records, financial information, or intellectual property.
Disruption of operations:
Zero-day vulnerability can be used to disrupt operations by disabling systems or networks. This can lead to financial losses, productivity losses, and damage to the organization’s reputation.
Various Forms of Zero-Day Threats
Zero-Day Exploits:
Attackers leverage previously unknown vulnerabilities in software or hardware to launch targeted attacks without any available patches or defenses.
Zero-Day Malware:
Malicious software that utilizes newly discovered vulnerabilities to infect systems and evade traditional security measures, remaining undetected until the vulnerability is exposed.
Zero-Day Worms:
Self-replicating malware that exploits unknown vulnerabilities to spread rapidly across networks, infecting multiple systems in a short time frame.
Zero-Day Ransomware:
Ransomware that exploits newly discovered weaknesses to encrypt data and demand a ransom, catching victims off guard with no immediate solution.
Zero-Day Phishing:
Advanced phishing techniques that exploit unknown vulnerabilities to trick users into divulging sensitive information or clicking on malicious links.
Zero-Day Botnets:
Botnets created by exploiting undisclosed flaws in devices or systems, enabling attackers to gain control over large networks for malicious purposes.
Zero-Day Denial-of-Service (DoS) Attacks:
DoS attacks that exploit new vulnerabilities, overwhelming targeted systems and disrupting their normal operations.
Zero-Day APTs (Advanced Persistent Threats):
Long-term and sophisticated cyber-espionage campaigns that exploit unknown vulnerabilities to infiltrate and remain undetected within high-value targets.
It’s important to note that zero-day threats continually evolve, making them particularly challenging for defenders to detect and mitigate effectively.
How to Detect Zero-Day Attacks
There is no silver bullet for detecting zero-day attacks. However, there are a number of steps that organizations can take to improve their chances of detecting and mitigating these attacks.
Here are some of the ways to detect zero-day attacks:
Use threat intelligence:
Threat intelligence can help organizations to identify emerging threats, including zero-day attacks. Threat intelligence providers collect and analyze information from a variety of sources, such as vulnerability databases, social media, and dark web forums. This information can be used to identify potential threats and to develop mitigation strategies.
Deploy next-generation antivirus (NGAV):
NGAV solutions use a variety of techniques to detect and block zero-day attacks, such as machine learning, behavioral analysis, and sandboxing. NGAV solutions can provide a layer of protection against zero-day attacks that traditional antivirus solutions cannot.
Use a web application firewall (WAF):
A WAF can be used to block malicious traffic that is targeting web applications. WAFs can also be used to filter out traffic that contains suspicious content, such as traffic that contains large amounts of data or traffic that is sent from unusual sources.
Implement a layered security approach:
A layered security approach involves using a variety of security controls, such as firewalls, intrusion detection systems, and antivirus software. By using a layered approach, organizations can improve their chances of detecting and mitigating zero-day attacks.
Use a security information and event management (SIEM) system:
A SIEM system can help organizations to collect and analyze security logs from a variety of sources. This information can be used to identify potential threats, such as zero-day attacks.
Use a honeypot:
A honeypot is a computer system that is designed to attract attackers. When an attacker tries to exploit a honeypot, the attacker’s activity can be monitored and analyzed. This information can be used to improve organizations’ defenses against zero-day attacks.
Use a sandbox:
A sandbox is a computer environment that is isolated from the rest of the network. When a suspicious file is uploaded to a sandbox, it can be executed in a safe environment without affecting the rest of the network. This can help organizations to identify zero-day attacks without putting their systems at risk.
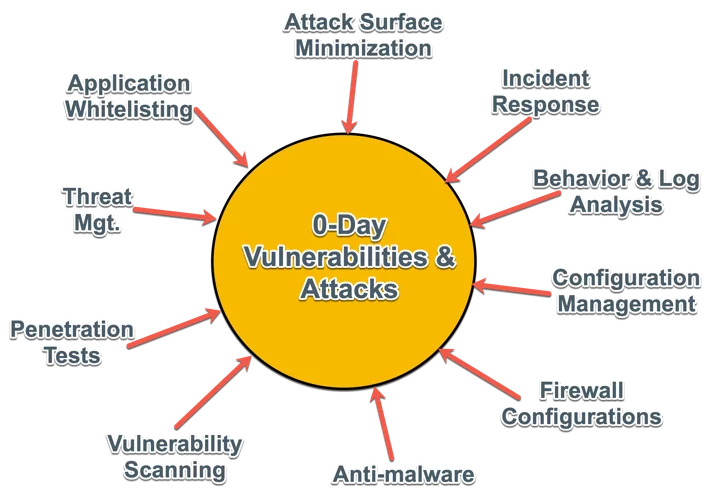
How to Mitigate Zero-Day Attacks
In addition to detecting zero-day attacks, organizations should also take steps to mitigate the damage caused by these attacks.

Mitigating Zero Day Attacks With a Detection, Prevention and Response Strategy – Spiceworks
Here are some of the ways to mitigate zero-day attacks:
Have a plan in place:
Organizations should have a plan in place for responding to zero-day attacks. This plan should include steps for identifying and containing the attack, as well as steps for recovering from the attack. Routine testing and timely updates are critical for the plan’s efficacy and adaptability.
Patch software promptly:
As soon as a patch for a known vulnerability is released, organizations should install it as soon as possible. This will help to protect against attacks that exploit known vulnerabilities.
Use strong passwords:
Organizations should use strong passwords for all accounts, including user accounts, administrative accounts, and service accounts. Strong passwords should be at least 12 characters long and should contain a mix of upper and lowercase letters, numbers, and symbols.
Safeguard Vigilance :
Enhance your defense with an IDS or IPS solution. While signature-based systems might miss the specific attack, they can still notify you of any unusual activities potentially linked to the incident.
Use a vulnerability management solution:
A vulnerability management solution can help organizations to identify and prioritize vulnerabilities in their systems. This information can be used to develop a plan for patching vulnerabilities and mitigating the risk of zero-day attacks.
Defending against attacks :
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) can detect suspicious activity that occurs as a side effect of an attack, even if they cannot identify the attack itself. This information can help defenders to investigate and respond to attacks more effectively.
Be careful about what you click:
Employees should be careful about what they click on, especially in emails and on websites. If an email or website looks suspicious, employees should not click on any links or open any attachments.
Use a secure internet connection:
Organizations should use a secure internet connection, such as a Virtual Private Network (VPN), when connecting to sensitive systems or data. This will help to protect against attacks that exploit vulnerabilities in public Wi-Fi networks.
By taking these steps, organizations can improve their chances of preventing or minimizing the damage caused by zero-day attacks.
Real World Examples
Stuxnet:
Stuxnet is one of the most well-known examples of a zero-day attack. It was a highly sophisticated worm discovered in 2010, specifically designed to target and disrupt Iran’s nuclear program. Stuxnet exploited multiple zero-day vulnerabilities in Microsoft Windows operating systems and Siemens industrial control systems (ICS) software, allowing it to silently spread and manipulate the programmable logic controllers (PLCs) responsible for controlling the centrifuges in Iran’s nuclear facilities.
Zoom :
In 2020, a critical vulnerability surfaced in the widely used video conferencing platform, Zoom. This zero-day attack exposed a significant security flaw, allowing hackers to gain remote access to a user’s PC, particularly if they were running an outdated version of Windows. For administrators, the consequences were even more severe, as the attackers could exploit the vulnerability to fully take control of their machines, granting access to sensitive files and data. This incident served as a stark reminder of the importance of prompt updates and robust security measures to safeguard against potential cyber threats in the digital landscape.
Microsoft Windows, Eastern Europe :
In 2019, the attackers exploited a flaw in Microsoft Windows that allowed them to gain more control over the system and targeted government institutions in Eastern Europe. They could run any code, install applications, and access and modify the data on the affected systems. The Microsoft Security Response Center was alerted of the attack and developed and deployed a patch to fix the flaw.
Conclusion
In conclusion, protecting businesses from zero-day attacks is critical in today’s threat landscape. While these attacks pose significant challenges due to their stealthy nature, organizations can bolster their defenses with proactive measures. By implementing the recommended tips, such as conducting regular vulnerability assessments, deploying advanced threat detection solutions, and educating employees about potential risks, businesses can enhance their security posture and better safeguard against zero-day vulnerabilities. Continuous vigilance and a strong preventive approach will empower organizations to minimize the impact of these elusive threats and protect their valuable assets and data.
Reference
https://www.kaspersky.co.in/resource-center/definitions/zero-day-exploit
https://www.manageengine.com/log-management/cyber-security/what-is-zero-day-exploit.html
https://www.thesecuritybuddy.com/data-breaches-prevention/what-is-a-zero-day-attack/
https://www.indusface.com/blog/steps-to-secure-zero-day-threats/
https://www.imperva.com/learn/application-security/zero-day-exploit/
https://learn.g2.com/zero-day-attack-prevention
https://www.ebcgroup.co.uk/news-insights/how-to-protect-your-business-against-zero-day-attacks
https://www.graphus.ai/blog/zero-day-threats-what-can-organizations-do-to-prevent-one-from-impacting-them/
https://www.manageengine.com/vulnerability-management/zero-day-vulnerability-mitigation.html
https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-zero-day-attack/how-to-prevent-zero-day-attacks/
https://www.techtarget.com/searchsecurity/definition/zero-day-vulnerability
https://www.portnox.com/blog/stopping-zero-day-attacks/
https://www.cloudflare.com/learning/security/ransomware/petya-notpetya-ransomware/
https://www.imperva.com/learn/application-security/wannacry-ransomware/
https://nordvpn.com/blog/stuxnet-virus/

